How Access Control Systems Work
What is an Access Control System?
An access control system is a form of physical security that manages the entry point to your business space or interior areas of a building. Access control systems act as gatekeepers to physically keep out unauthorized users, while letting authorized users enter an area. Some access control systems can also track who enters or leaves secure areas. The most basic example of an access control system is a lock and key.
How Does Access Control Work?
There are five general steps of access control systems:
-
Authentication
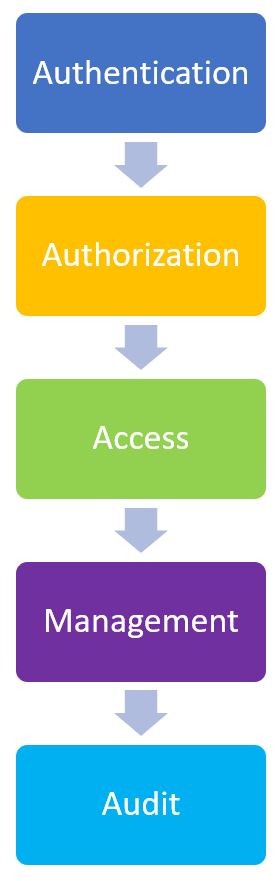
5-step process for how access control systems work First things first, a credential is authenticated. Once a user presents their credential to a reader/controller and data is validated to determine whether the credential is known or recognized by the system.
-
Authorization
Next, the reader/controller establishes if the user is authorized to access the entry point. For the user to be authorized, the reader/controller must answer a few questions. Does the user have access to the door or entry point they’re requesting? Is the user using an allowed credential type, such as a mobile app or key fob? Is the request being made within a defined schedule? Are there any security restrictions in place, such a system lockdown?
-
Access
After authorization is decided, the reader/controller sends a message to trigger the door hardware to unlock the entry point. If the door unlocks, the system then tracks the user triggering the unlocking.
-
Management
Administering tasks for an access control system can include adding or removing users, activity, credentials, schedules, and alerts. Most access control systems use administrative software that automatically syncs with a reader/controller. Cloud-based software allows administrators to access their access control systems anywhere and anytime.
-
Audit
Most access control systems offer an audit option, allowing administrators to generate reports for access logs including entry activity. Reports can help meet compliance standards and ensure the system is working as expected.
Access control system authenticates a user’s identity based on their credentials via a reader installed near an entry. The reader references an Access Control Unit (ACU), often called an access control panel or controller, to determine the authorization level. The controller is often embedded in the reader so only one piece of hardware is needed. If authorized, the ACU triggers the door hardware at the entry to unlock. All of the equipment is then managed by a software application that defines users, credentials, access schedules, entries, and more.
Types of Credentials for Access Control Systems
The physical entry points to your facility must have an electronic locking mechanism such as a door strike or maglock that locks and unlocks doors. The door opens only if an authorized person has the proper credentials. There are various credentials people can present:
Key Fob or Access Card
 A key fob or access card is a physical card a person can swipe on scan for entry. A physical card is a popular choice since it is what is most widely known as an access control option. But key cards are also easy to lose, share, or steal. Most key cards and fobs use Radio Frequency Identification (RFID) technology, meaning the cards contain encoded microchips that are interrogated by radio waves. Thieves understand this, which is why key-copying kiosks pose a new security threat. Plus, there’s the time-intensive management and ongoing cost of key card/fob systems.
A key fob or access card is a physical card a person can swipe on scan for entry. A physical card is a popular choice since it is what is most widely known as an access control option. But key cards are also easy to lose, share, or steal. Most key cards and fobs use Radio Frequency Identification (RFID) technology, meaning the cards contain encoded microchips that are interrogated by radio waves. Thieves understand this, which is why key-copying kiosks pose a new security threat. Plus, there’s the time-intensive management and ongoing cost of key card/fob systems.
Password or Pin Code
 A password or pin code is something an approved user knows and enters into a keypad. Some systems may only accept one master pin code, or users can each have a personal pin code. Pin codes or passwords can be problematic as they are easily forgotten or shared. If there’s only one code (not personal codes for each employee), it has to be changed each time an employee leaves the company. The keypads can also be easily hacked to short the wires.
A password or pin code is something an approved user knows and enters into a keypad. Some systems may only accept one master pin code, or users can each have a personal pin code. Pin codes or passwords can be problematic as they are easily forgotten or shared. If there’s only one code (not personal codes for each employee), it has to be changed each time an employee leaves the company. The keypads can also be easily hacked to short the wires.
Biometrics
 Biometrics include fingerprints, palm veins, or retinas and are used to identify the person accessing the area. Biometric readers can range from low-end fingerprint scanners to high-end multi-input readers. The downsides to biometric readers are their sensitivity in inclement weather, dust, sand, or humid environments, as well as various hygiene issues (many property owners/managers are switching to touchless entry systems).
Biometrics include fingerprints, palm veins, or retinas and are used to identify the person accessing the area. Biometric readers can range from low-end fingerprint scanners to high-end multi-input readers. The downsides to biometric readers are their sensitivity in inclement weather, dust, sand, or humid environments, as well as various hygiene issues (many property owners/managers are switching to touchless entry systems).
Smartphone Apps

A mobile app using Bluetooth allows approved users to simply use their smartphone to unlock entry points after they’ve installed the app. Users are assigned mobile credentials or digital “Smart Keys”. The unlock request can be made a few ways – tapping a button in the app, holding the phone up to the reader, or touching the reader with their hand with the phone in their pocket. Authorization requests transmit via Bluetooth, Wi-Fi, or cellular data.
Mobile credentials are cost-effective, secure, and encrypted. With frequent app updates, users automatically receive the newest features and enhancements. Plus, most people are never without their smartphones, meaning the risk of someone sharing their key (smartphone) with an unauthorized person is lower than a keycard, code, or physical key.

There are two main ways that a phone can open a door using Bluetooth:
- Smart lock with the reader in the door handle.
- Reader next to the door or gate.
Which Bluetooth option should you pick?
If a door already has a Wiegand door controller, then you really only need the Bluetooth reader that can connect to it.
If a door does not already have a Wiegand door controller, then the simplest option is to use the battery-powered commercial smart lock.
So What?
Your access control system is an essential aspect of your building’s security. It provides an extra layer of protection to control and monitor access to your business. If you’re looking for cost-effective access control solutions, VIZpin offers both smart locks (unlock door with phone) and Bluetooth access control readers (that go on the wall beside a door).
